CMS漏洞检测工具 – CMSmap
- 发表于
- 安全工具
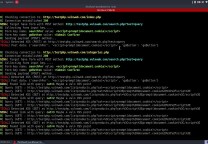
CMSmap是一个Python编写的针对开源CMS(内容管理系统)的安全扫描器,它可以自动检测当前国外最流行的CMS的安全漏洞。 CMSmap主要是在一个单一的工具集合了不同类型的CMS的常见的漏洞。CMSmap目前只支持WordPress,Joomla和Drupal。
安装
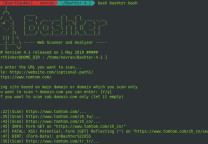
Cloning最新 CMSmap版本:
| 1 | git clone https://github.com/Dionach/CMSmap.git |
使用
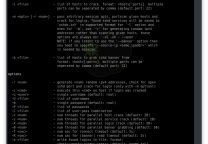
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 | CMSmap tool v0.6 - Simple CMS Scanner Author: Mike Manzotti mike.manzotti@dionach.com Usage: cmsmap.py -t <URL> Targets: -t, --target target URL (e.g. 'https://example.com:8080/') -f, --force force scan (W)ordpress, (J)oomla or (D)rupal -F, --fullscan full scan using large plugin lists. False positives and slow! -a, --agent set custom user-agent -T, --threads number of threads (Default: 5) -i, --input scan multiple targets listed in a given text file -o, --output save output in a file --noedb enumerate plugins without searching exploits Brute-Force: -u, --usr username or file -p, --psw password or file --noxmlrpc brute forcing WordPress without XML-RPC Post Exploitation: -k, --crack password hashes file (Require hashcat installed. For WordPress and Joomla only) -w, --wordlist wordlist file Others: -v, --verbose verbose mode (Default: false) -U, --update (C)MSmap, (W)ordpress plugins and themes, (J)oomla components, (D)rupal modules, (A)ll -h, --help show this help Examples: cmsmap.py -t https://example.com cmsmap.py -t https://example.com -f W -F --noedb cmsmap.py -t https://example.com -i targets.txt -o output.txt cmsmap.py -t https://example.com -u admin -p passwords.txt cmsmap.py -k hashes.txt -w passwords.txt |
原文连接:CMS漏洞检测工具 – CMSmap 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。