Sifter:一个osint(开源网络情报)侦察和漏洞扫描程序
- 发表于
- 安全工具
Sifter介绍
一个osint(开源网络情报)侦察和漏洞扫描程序。枚举非常重要,它在不同的模块集中结合了一系列工具,以便快速执行侦察任务,检查网络防火墙,枚举远程和本地主机以及扫描microsft中的“蓝色”漏洞,如果未修补,请加以利用。它使用blackwidow和konan之类的工具进行Webdir枚举,并使用ASM快速进行攻击面映射。
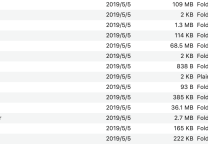
收集的信息将保存到结果文件夹,这些输出文件可以轻松解析到TigerShark,以便在您的广告系列中使用。或编制最终报告以完成渗透测试。
Sifter安装与使用
最新版本可在这里下载
或使用推荐的git方式
| 1 2 3 4 5 6 | * This will download and install all required tools * $ git clone https://github.com/s1l3nt78/sifter.git $ cd sifter $ chmod +x install.sh $ ./install.sh |
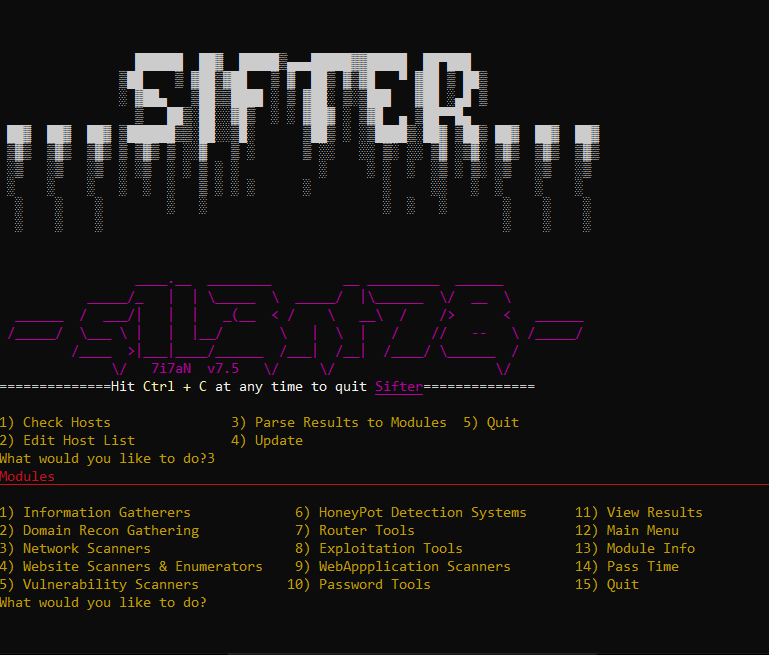
Sifter使用的一些Modules
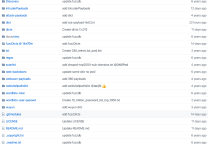
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 | # Information Modules = Enterprise Information Gatherers -theHarvester - https://github.com/laramies/theHarvester -Osmedeus - https://github.com/j3ssie/Osmedeus -ReconSpider - https://github.com/bhavsec/reconspider -CredNinja - -CredNinja - https://github.com/Raikia/CredNinja = Targeted Information Gatherers -Maryam - https://github.com/saeeddhqan/Maryam -Seeker - https://github.com/thewhiteh4t/seeker -Sherlock - https://github.com/sherlock-project/sherlock -xRay - https://github.com/evilsocket/xray # Domain Recon Gathering -DnsTwist - https://github.com/elceef/dnstwist -Armory - https://github.com/depthsecurity/armory -SayDog - https://github.com/saydog/saydog-framework # Router Tools -MkCheck - https://github.com/s1l3nt78/MkCheck -RouterSploit - https://github.com/threat9/routersploit # Exploitation Tools = MS Exploiters -ActiveReign - https://github.com/m8r0wn/ActiveReign -iSpy - https://github.com/Cyb0r9/ispy -SMBGhost --SMBGhost Scanner - https://github.com/ioncube/SMBGhost --SMBGhost Exploit - https://github.com/chompie1337/SMBGhost_RCE_PoC = Website Exploiters -DDoS --Dark Star - https://github.com/s1l3nt78/Dark-Star --Impulse - https://github.com/LimerBoy/Impulse -NekoBot - https://github.com/tegal1337/NekoBotV1 -xShock - https://github.com/capture0x/XSHOCK -VulnX - https://github.com/anouarbensaad/vulnx = Exploit Searching -FindSploit - https://github.com/1N3/Findsploit -ShodanSploit - https://github.com/shodansploit/shodansploit -TigerShark (Phishing) - https://github.com/s1l3nt78/TigerShark = Post-Exploitation -EoP Exploit (Elevation of Priviledge Exploit) - https://github.com/padovah4ck/CVE-2020-0683 -Omega - https://github.com/entynetproject/omega -WinPwn - https://github.com/S3cur3Th1sSh1t/WinPwn -CredHarvester - https://github.com/Technowlogy-Pushpender/creds_harvester -PowerSharp - https://github.com/S3cur3Th1sSh1t/PowerSharpPack -ACLight2 - https://github.com/cyberark/ACLight =FuzzyDander - Equation Group, Courtesy of the Shadow Brokers (Obtained through issue request.) -FuzzBunch -Danderspritz =BruteDUM (Bruteforcer) - https://github.com/GitHackTools/BruteDum # Password Tools -Mentalist - https://github.com/sc0tfree/mentalist -DCipher - https://github.com/k4m4/dcipher # Network Scanners -Nmap - https://nmap.org -AttackSurfaceMapper - https://github.com/superhedgy/AttackSurfaceMapper -aSnip - https://github.com/harleo/asnip -wafw00f - https://github.com/EnableSecurity/wafw00f -Arp-Scan # HoneyPot Detection Systems -HoneyCaught - https://github.com/aswinmguptha/HoneyCaught -SniffingBear - https://github.com/MrSuicideParrot/SniffingBear -HoneyTel (telnet-iot-honeypot) - https://github.com/Phype/telnet-iot-honeypot # Vulnerability Scanners -Flan - https://github.com/cloudflare/flan -Rapidscan - https://github.com/skavngr/rapidscan -Yuki-Chan - https://github.com/Yukinoshita47/Yuki-Chan-The-Auto-Pentest # WebApplication Scanners -Sitadel - https://github.com/shenril/Sitadel -OneFind - https://github.com/nyxgeek/onedrive_user_enum -AapFinder - https://github.com/Technowlogy-Pushpender/aapfinder -BFAC - https://github.com/mazen160/bfac -XSStrike - https://github.com/s0md3v/XSStrike # Website Scanners & Enumerators -Nikto - https://github.com/sullo/nikto -Blackwidow - https://github.com/1N3/blackwidow -Wordpress ---WPScan - https://github.com/wpscanteam/wpscan ---WPForce/Yertle - https://github.com/n00py/WPForce -Zeus-Scanner - https://github.com/Ekultek/Zeus-Scanner -Dirb -DorksEye - https://github.com/BullsEye0/dorks-eye # Web Mini-Games -This was added in order to have a fun way to pass time during the more time intensive modules. Such as nMap Full Port scan or a RapidScan run. |
Sifter帮助菜单
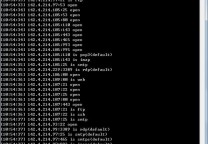
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | $ sifter runs the programs bringing up the menu in a cli environment $ sifter -c will check the existing hosts in the hostlist $ sifter -a 'target-ip' appends the hostname/IP to host file $ sifter -m Opens the Main Module menu $ sifter -e Opens the Exploitation Modules $ sifter -i Opens the Info-based Module menu $ sifter -d Opens the Domain Focused Modules $ sifter -n Opens the Network Mapping Modules menu $ sifter -w Opens the Website Focused Modules $ sifter -wa Opens the Web-App Focused Module menu $ sifter -p opens the password tools for quick passlist generation or hash decryption $ sifter -v Opens the Vulnerability Scanning Module Menu $ sifter -r Opens the results folder for easy viewing of all saved results $ sifter -u Checks for/and installs updates $ sifter -h This Help Menu |
原文连接:Sifter:一个osint(开源网络情报)侦察和漏洞扫描程序 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。