PEpper – PE文件恶意软件静态分析的开源脚本
- 发表于
- 安全工具
PEpper PE文件分析
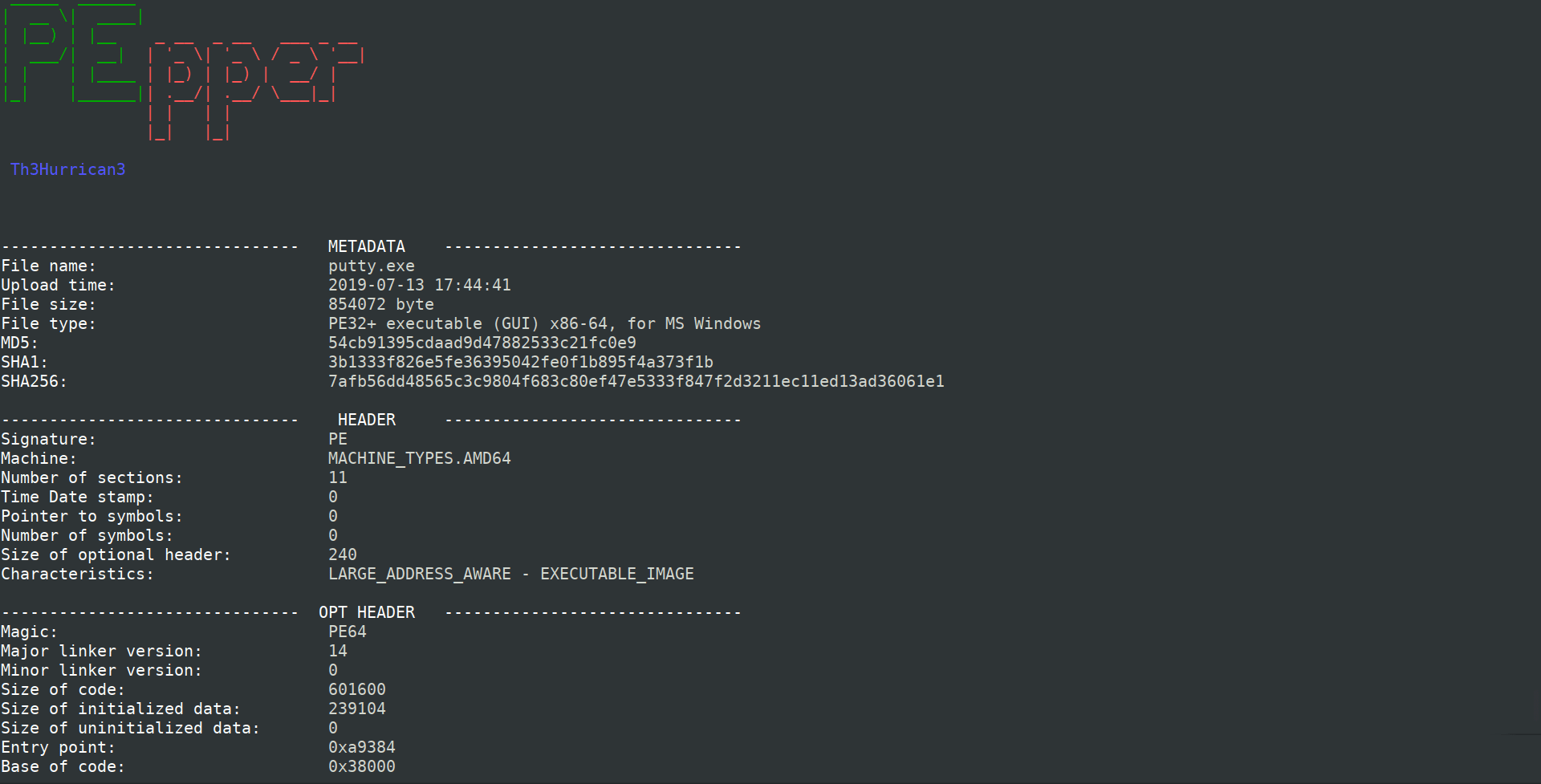
一个开源的PE文件恶意分析脚本,用于对PE执行恶意软件静态分析。PE(Portable Executable)格式,是微软环境可移植可执行文件(如exe、dll、vxd、sys和vdm等)的标准文件格式。

PEpper 安装
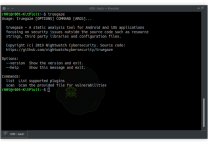
eva@paradise:~$ git clone https://github.com/Th3Hurrican3/PEpper/
eva@paradise:~$ cd PEpper
eva@paradise:~$ pip3 install -r requirements.txt
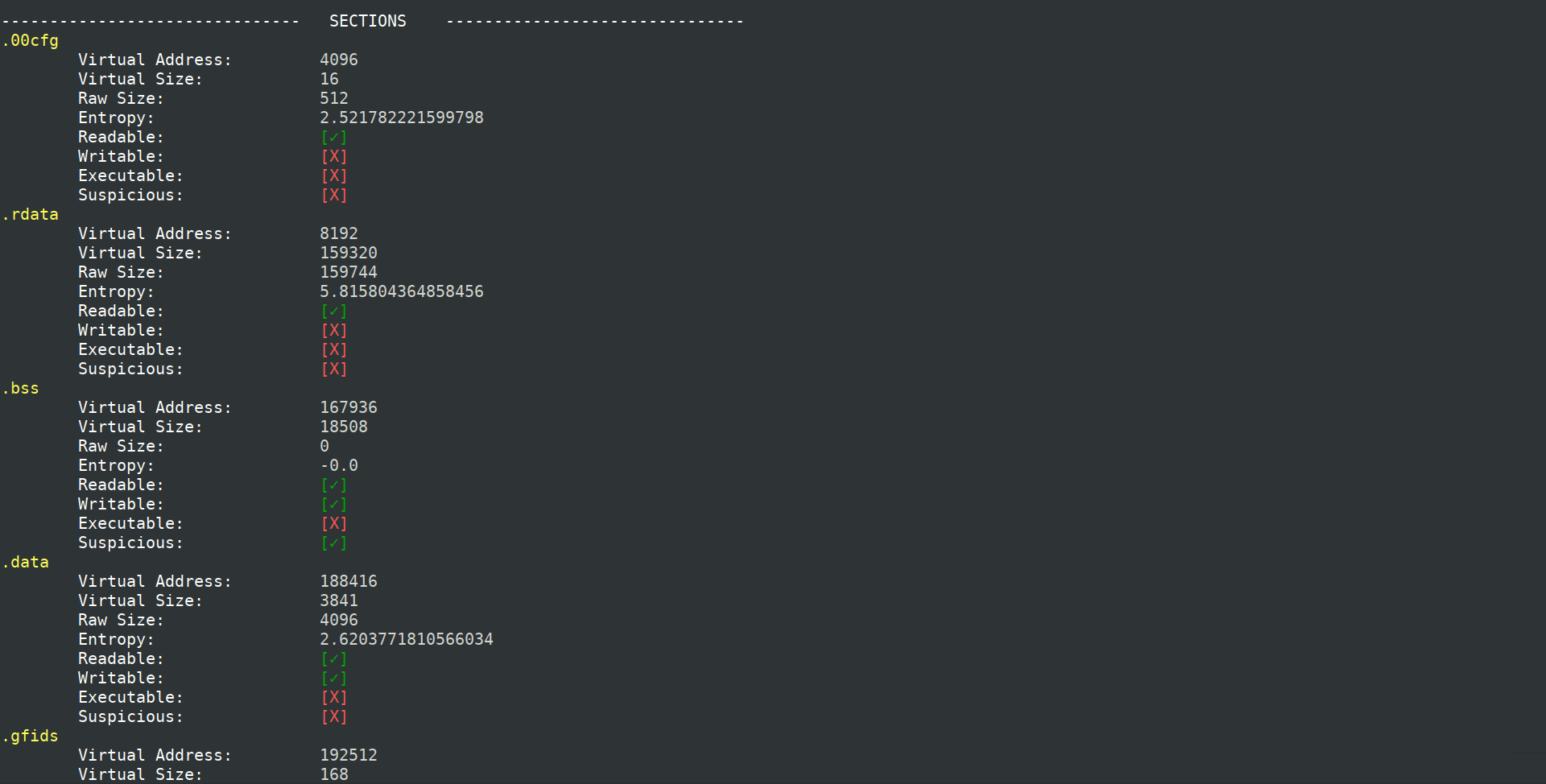
eva@paradise:~$ python3 pepper.py ./malware_dir截图
CSV输出
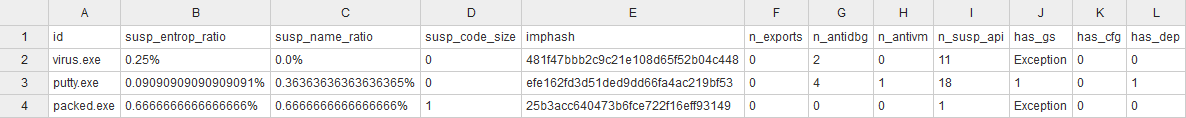
特征提取
- Suspicious entropy ratio
- Suspicious name ratio
- Suspicious code size
- Suspicious debugging time-stamp
- Number of export
- Number of anti-debugging calls
- Number of virtual-machine detection calls
- Number of suspicious API calls
- Number of suspicious strings
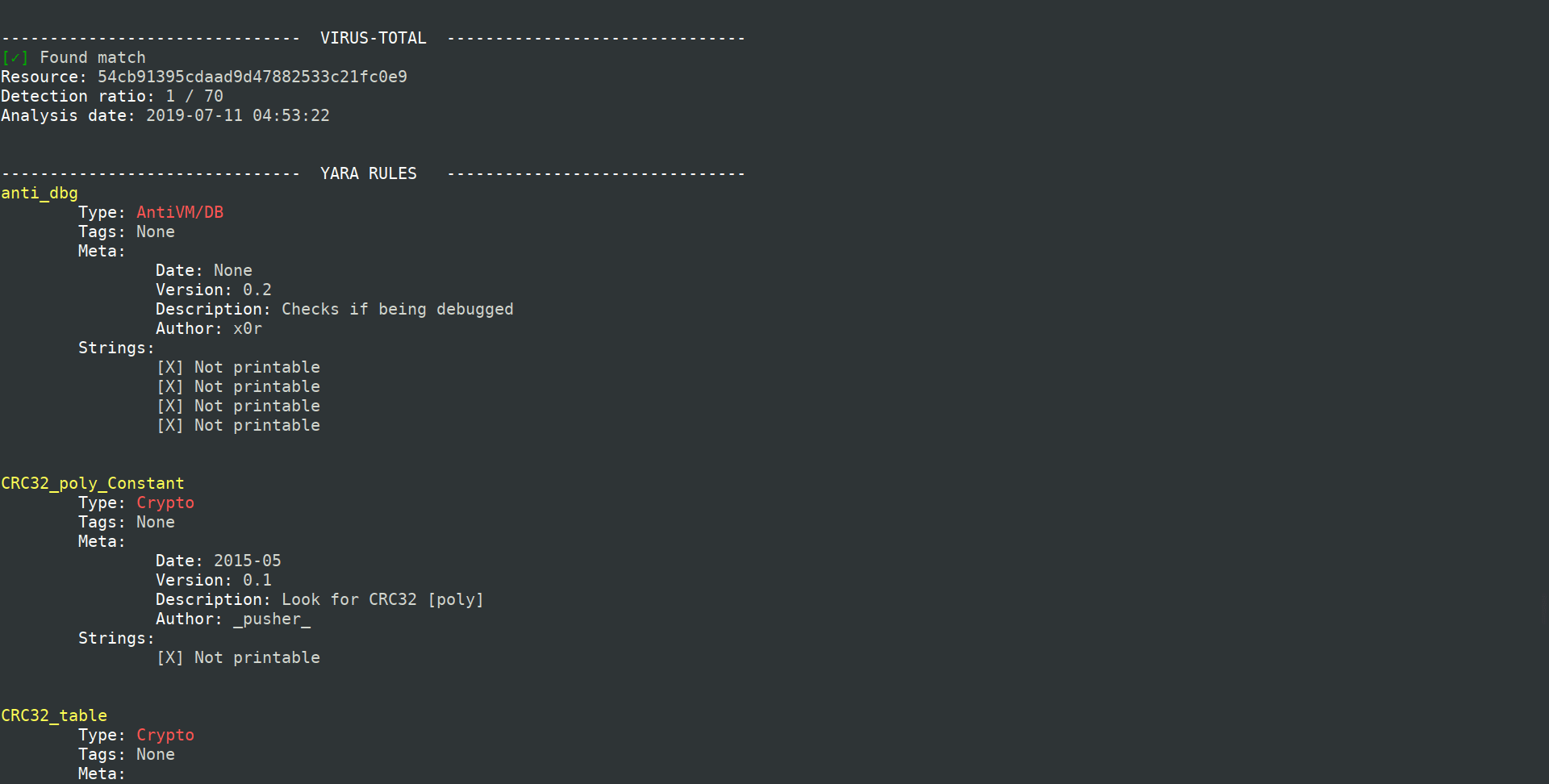
- Number of YARA rules matches
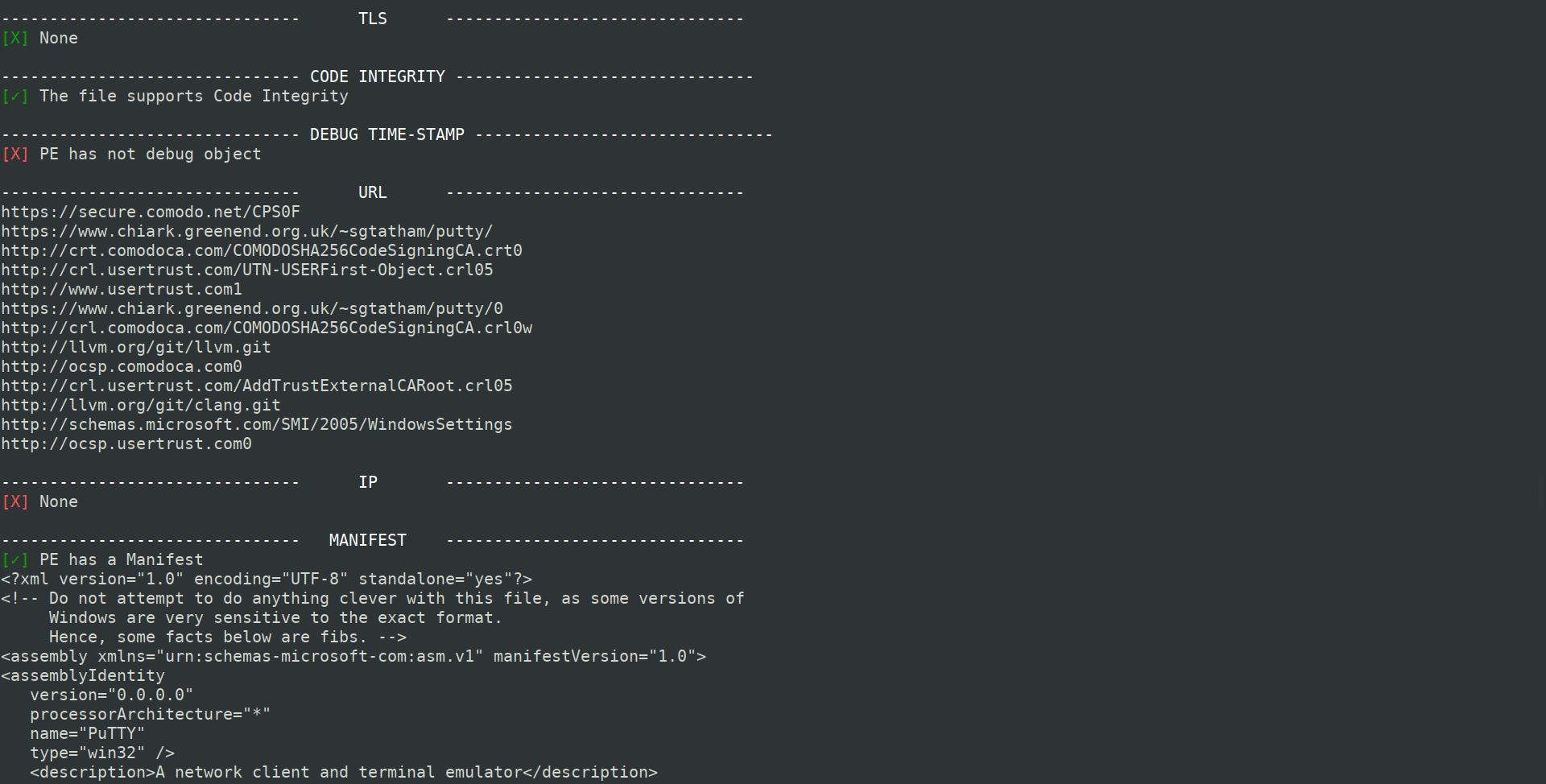
- Number of URL found
- Number of IP found
- Cookie on the stack (GS) support
- Control Flow Guard (CFG) support
- Data Execution Prevention (DEP) support
- Address Space Layout Randomization (ASLR) support
- Structured Exception Handling (SEH) support
- Thread Local Storage (TLS) support
- Presence of manifest
- Presence of version
- Presence of digital certificate
- Packer detection
- VirusTotal database detection
- Import hash
原文连接:PEpper – PE文件恶意软件静态分析的开源脚本
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。