usbrip:Linux上跟踪USB设备的CLI取证工具
- 发表于
- 安全工具
usbrip 取证工具
usbrip(源自“USB Ripper”,而不是“USB RIP”)是一个带有CLI界面的开源取证工具,可以让您在Linux机器上跟踪USB设备(即USB事件历史记录,“已连接”和“已断开连接”事件)。
usbrip是用Python 3编写的软件,它解析Linux日志文件(
/var/log/syslog*
或
/var/log/messages*
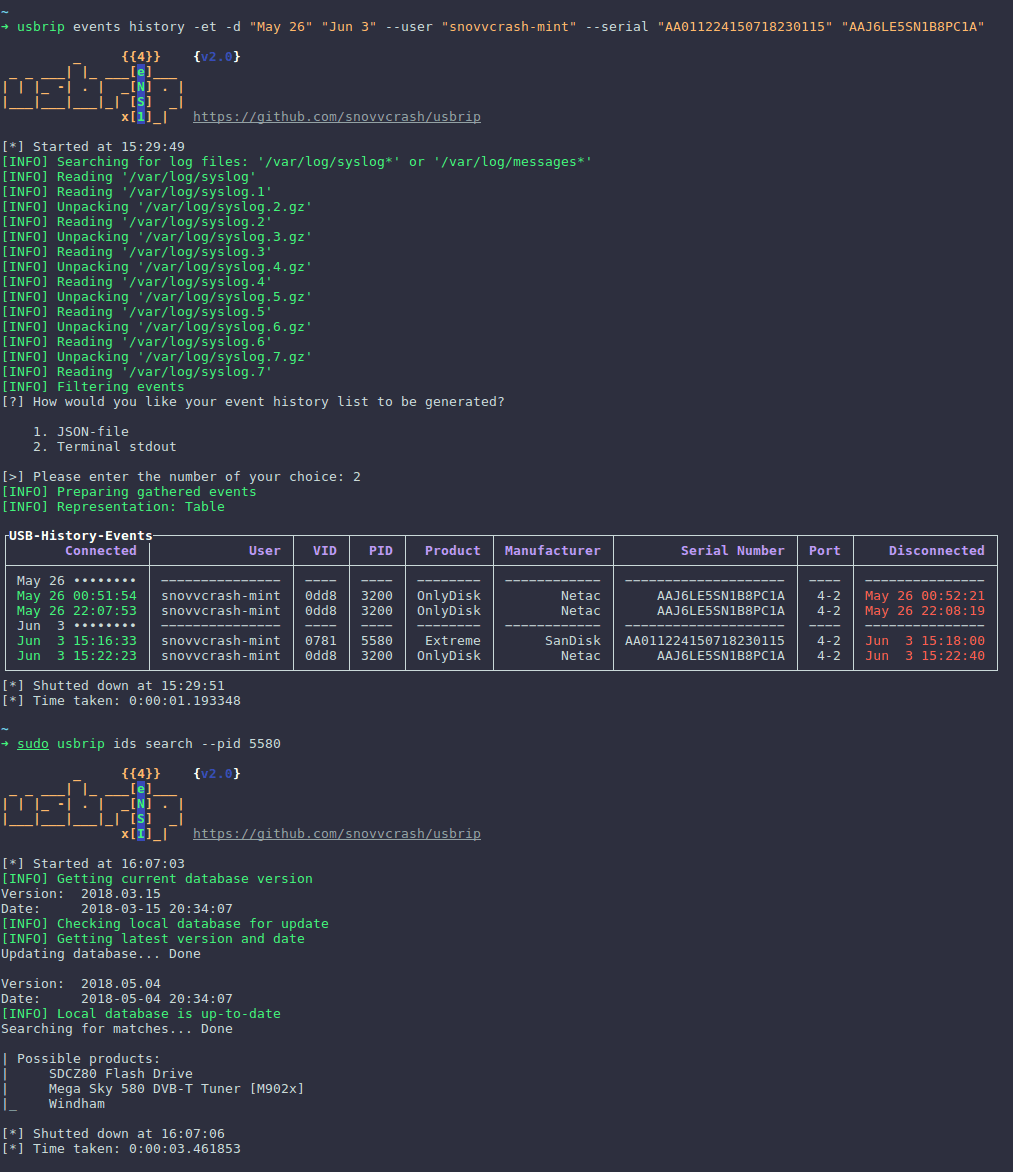
)以构建USB事件历史表。此类表格可能包含以下列:“已连接”(日期和时间),“用户”,“VID”(供应商ID),“PID”(产品ID),“产品”,“制造商”,“序列号”, “端口”和“断开连接”(日期和时间)。
此外,它还可以:
- 导出收集的信息作为JSON转储;
- 生成一个授权(可信)USB设备列表作为JSON(称之为
auth.json); - 根据以下内容搜索“违规事件”
auth.json:show(或生成另一个JSON)USB设备出现在历史记录中并且不会出现在auth.json; - *使用
-sflag * 安装时,创建加密存储(7zip存档),以便在crontab调度程序的帮助下自动备份和累积USB事件; - 根据其VID和/或PID搜索有关特定USB设备的其他详细信息。
usbrip 安装
快速安装
usbrip可在PyPI下载和安装:
| 1 | $ pip3 install usbrip |
Git安装
| 1 2 3 4 5 6 | # 下载 ~$ git clone https://github.com/snovvcrash/usbrip.git usbrip && cd usbrip ~/usbrip$ # 安装依赖 ~$ sudo apt install python3-venv p7zip-full -y |
有两种方法可以将usbrip安装到系统中:
pip
或
setup.py
。
pip
要么
setup.py
首先,usbrip是pip可安装的。这意味着在git克隆了repo之后你可以简单地启动pip安装过程,然后在终端的任何地方运行usbrip,如下所示:
| 1 2 3 4 5 | ~/usbrip$ python3 -m venv venv && source venv/bin/activate (venv) ~/usbrip$ pip install . (venv) ~/usbrip$ usbrip -h |
或者,如果要在本地解析Python依赖关系(不打扰PyPI),请使用
setup.py
:
| 1 2 3 4 5 | ~/usbrip$ python3 -m venv venv && source venv/bin/activate (venv) ~/usbrip$ python setup.py install (venv) ~/usbrip$ usbrip -h |
注意:您可能希望在Python虚拟环境处于活动状态时运行安装过程(如上所示)。
usbrip 使用
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 | # ---------- BANNER ---------- $ usbrip banner Get usbrip banner. # ---------- EVENTS ---------- $ usbrip events history [-t | -l] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [-c <COLUMN> [<COLUMN> ...]] [-f <FILE> [<FILE> ...]] [-q] [--debug] Get USB event history. $ usbrip events open <DUMP.JSON> [-t | -l] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [-c <COLUMN> [<COLUMN> ...]] [-f <FILE> [<FILE> ...]] [-q] [--debug] Open USB event dump. $ usbrip events gen_auth <OUT_AUTH.JSON> [-a <ATTRIBUTE> [<ATTRIBUTE> ...]] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [-f <FILE> [<FILE> ...]] [-q] [--debug] Generate a list of trusted (authorized) USB devices. $ usbrip events violations <IN_AUTH.JSON> [-a <ATTRIBUTE> [<ATTRIBUTE> ...]] [-t | -l] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [-c <COLUMN> [<COLUMN> ...]] [-f <FILE> [<FILE> ...]] [-q] [--debug] Get USB violation events based on the list of trusted devices. # ---------- STORAGE ---------- $ usbrip storage list <STORAGE_TYPE> [-q] [--debug] List contents of the selected storage (7zip archive). STORAGE_TYPE is "history" or "violations". $ usbrip storage open <STORAGE_TYPE> [-t | -l] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [-c <COLUMN> [<COLUMN> ...]] [-q] [--debug] Open selected storage (7zip archive). Behaves similary to the EVENTS OPEN submodule. $ usbrip storage update <STORAGE_TYPE> [-a <ATTRIBUTE> [<ATTRIBUTE> ...]] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [--lvl <COMPRESSION_LEVEL>] [-q] [--debug] Update storage — add USB events to the existing storage (7zip archive). COMPRESSION_LEVEL is a number in [0..9]. $ usbrip storage create <STORAGE_TYPE> [-a <ATTRIBUTE> [<ATTRIBUTE> ...]] [-e] [-n <NUMBER_OF_EVENTS>] [-d <DATE> [<DATE> ...]] [--user <USER> [<USER> ...]] [--vid <VID> [<VID> ...]] [--pid <PID> [<PID> ...]] [--prod <PROD> [<PROD> ...]] [--manufact <MANUFACT> [<MANUFACT> ...]] [--serial <SERIAL> [<SERIAL> ...]] [--port <PORT> [<PORT> ...]] [--lvl <COMPRESSION_LEVEL>] [-q] [--debug] Create storage — create 7zip archive and add USB events to it according to the selected options. $ usbrip storage passwd <STORAGE_TYPE> [--lvl <COMPRESSION_LEVEL>] [-q] [--debug] Change password of the existing storage. # ---------- IDs ---------- $ usbrip ids search [--vid <VID>] [--pid <PID>] [--offline] [-q] [--debug] Get extra details about a specific USB device by its <VID> and/or <PID> from the USB ID database. $ usbrip ids download [-q] [--debug] Update (download) the USB ID database. |
示例
显示所有USB设备的事件历史
| 1 | $ usbrip events history -ql -n 100 |
显示外部USB设备的事件历史
| 1 | $ usbrip events history -et -c conn vid pid disconn serial -d "Dec 9" "Dec 10" -f /var/log/syslog.1 /var/log/syslog.2.gz |
更多使用及说明请看readme。
原文连接:usbrip:Linux上跟踪USB设备的CLI取证工具 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。