加速乐Cookie破解与生成__jsl_clearance
- 发表于
- 周边
这是一个典型的反爬虫场景技术,我们知道使用了加速乐解析的站点是无法直接爬取的,因为它有一段JS校验(__jsl_clearance),校验不对不会返回任何内容。典型的操作手法是使用模拟器爬,但这样会使成本增加和效率会降低。今天分享的是加速乐Cookie破解与生成JS效验码。
加速乐Cookie破解
我用charles抓包发现,第一个请求返回的状态码是521的在这个页面
var x="createElement@fromCharCode@0@@https@5@@18@@Oct@toLowerCase@search@g@3@captcha@setTimeout@a@@@href@chars@8@addEventListener@@match@rOm9XFMtA3QKV7nYsPGT4lifyWwkq5vcjH2IdxUoCbhERLaz81DNB6@GMT@@onreadystatechange@@@WsAkM@charAt@length@@@@@@@@function@reverse@Array@@479@Path@@@replace@wH@var@tCX@DOMContentLoaded@attachEvent@Wed@location@28@catch@@if@String@@HY@return@try@D@while@@cookie@eval@@pathname@else@1@RegExp@split@@1539775703@6@@@innerHTML@@d@challenge@B@Expires@JgSe0upZ@1500@0xEDB88320@for@document@div@@join@@@17@12@f@@@@@parseInt@toString@@23@@charCodeAt@0xFF@mT@new@@E@__jsl_clearance@@36@@@window@2@false@firstChild@e@@substr".replace(/@*$/,"").split("@"),y="1l 21=1b(){g('1q.k=1q.2b+1q.c.1j(/[\\?|&]f-2o/,\\'\\')',2s);30.28='3o=2h.1f|3|'+(1b(){1l 3h=[1b(21){23 21},1b(3h){23 3h},(1b(){1l 21=30.1('31');21.2l='<h k=\\'/\\'>43</h>';21=21.41.k;1l 3h=21.p(/5?:\\/\\//)[3];21=21.44(3h.13).b();23 1b(3h){2u(1l 43=3;43<3h.13;43++){3h[43]=21.12(3h[43])};23 3h.33('')}})(),1b(21){2u(1l 3h=3;3h<21.13;3h++){21[3h]=3d(21[3h]).3e(3q)};23 21.33('')}],21=[[(-~(+[])+[]+[])+[-~!/!/+((+!-[])<<(+!-[]))+6]],'3k',[(-~(+[])+[]+[])+[(-~{}|3u)]],'1k',[[2i]],[(-~(+[])+[]+[])+[-~[-~!/!/+((+!-[])<<(+!-[]))-~!/!/+((+!-[])<<(+!-[]))]]],'3n%',[-~!/!/-~!/!/],'2p',[(-~(+[])+[]+[])+[3u+3u],(-~(+[])+[]+[])+(-~[]+((+!-[])<<-~!/!/+((+!-[])<<(+!-[])))+[]+[[]][3])],'11',[~~''],'1m',[((-~!/!/-~!/!/^-~(+[])))/~~''+[]+[]][3].12(~~!{}),[(-~(+[])+[]+[])+(-~[]+((+!-[])<<-~!/!/+((+!-[])<<(+!-[])))+[]+[[]][3])],'22',[(-~{}+[~~{}])/[3u]]+[3u+3u],'%',[(-~{}|3u)],'25'];2u(1l 43=3;43<21.13;43++){21[43]=3h[[e,2d,3u,2d,3u,e,2d,3,2d,e,2d,3,2d,3,e,2d,3,2d,3,2d][43]](21[43])};23 21.33('')})()+';2q=1p, 36-a-8 37:1r:3g r;1g=/;'};1u((1b(){24{23 !!3t.n;}1s(42){23 40;}})()){30.n('1n',21,40)}2c{30.1o('t',21)}",f=function(x,y){var a=0,b=0,c=0;x=x.split("");y=y||99;while((a=x.shift())&&(b=a.charCodeAt(0)-77.5))c=(Math.abs(b)<13?(b+48.5):parseInt(a,36))+y*c;return c},z=f(y.match(/\w/g).sort(function(x,y){return f(x)-f(y)}).pop());while(z++)try{eval(y.replace(/\b\w+\b/g, function(y){return x[f(y,z)-1]||("_"+y)}));break}catch(_){}不带上Cookie是无法访问站点的,
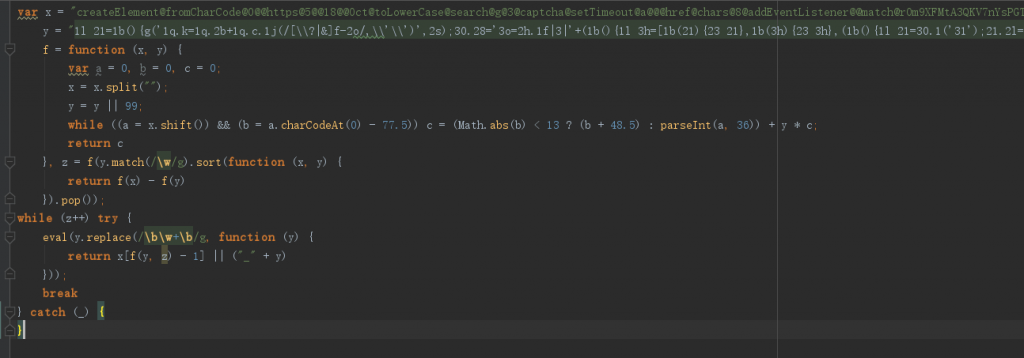
上面是还原代码 那么下面呢
try {
eval(y.replace(/\b\w+\b/g, function (y) {
return x[f(y, z) - 1] || ("_" + y)
}));
break
} catch (_) {
}这段代码是一次又一次不断地试错代码 直到出现可以执行的,我们看下怎么构造他,让他能输出正常代码
以下有两种思路
- 根据加速乐需要的对象构造函数
- 用特征判断eval是否成功
此处我用的第二种
通过运行我们可以推断出 正常代码如下
var _1u=function(){setTimeout('location.href=location.pathname+location.search.replace(/[\?|&]captcha-challenge/,\'\')',1500);document.cookie='__jsl_clearance=1539695410.624|0|'+(function(){var _u=[function(_1u){return eval('String.fromCharCode('+_1u+')')},(function(){var _1u=document.createElement('div');_1u.innerHTML='<a href=\'/\'>_2z</a>';_1u=_1u.firstChild.href;var _u=_1u.match(/https?:\/\//)[0];_1u=_1u.substr(_u.length).toLowerCase();return function(_u){for(var _2z=0;_2z<_u.length;_2z++){_u[_2z]=_1u.charAt(_u[_2z])};return _u.join('')}})()],_2z=[[((2^-~{})+[])+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+[~~!{}],[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]]+[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]],[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]],((2^-~{})+[])+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+[~~!{}],[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]]+[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]],[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+[(+!-{})],[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])],(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]]+[-~(((-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))*[(-~-~!![{}][(+!-{})]<<-~{})])],[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]]+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])],[[~~!{}]],[(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+[~~!{}],(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+((-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[]),[(+!-{})]+[~~!{}]+[(+!-{})],[(+!-{})]+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]+[(+!-{})],(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])+[(+!-{})],(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])+((2^-~{})+[]),[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+[-~(((-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))*[(-~-~!![{}][(+!-{})]<<-~{})])],((2^-~{})+[])+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+[~~!{}],(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])+[~~!{}]],[(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])],[[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]],[(+!-{})]+[(+!-{})]+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+((2^-~{})+[])],[[(+!-{})]+[(+!-{})]],[(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+((-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[]),(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0])+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])],[-~(((-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))*[(-~-~!![{}][(+!-{})]<<-~{})])]+[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]],[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]+((2^-~{})+[])],[[(+!-{})]+((2^-~{})+[])],[((2^-~{})+[])+(2-~(+[])+(-~(+[])<<(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})]))+[[]][0]),(((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]+[]+[])+[(+!-{})],[((+!-{})+[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])])/[(-~!![{}][(+!-{})]<<-~!![{}][(+!-{})])]]+[-~[-~(+[])-~(+[])]+((+!-{})+[(+!/!/)])/[-~-~!![{}][(+!-{})]]]]];for(var _1u=0;_1u<_2z.length;_1u++){_2z[_1u]=_u.reverse()[[(+!-{})]](_2z[_1u])};return _2z.join('')})()+';Expires=Tue, 16-Oct-18 14:10:10 GMT;Path=/;'};if((function(){try{return !!window.addEventListener;}catch(e){return false;}})()){document.addEventListener('DOMContentLoaded',_1u,false)}else{document.attachEvent('onreadystatechange',_1u)}我们将 __jsl_clearance=15 作为特征 构造代码如下
function getJSL(){
var data="";
while(data.indexOf('__jsl_clearance=15') === -1 && z++){
data = y.replace(/\b\w+\b/g, function(y){return x[f(y,z)-1]||("_"+y)});
}
return data;
}通过这串代码我们可以还原出正确执行的代码
但是
What?还有层加密? 人家Cloudflare只有一层,而且你们这也太相似了吧,用的同一种加密法,不管了,我们往下面看
var _21 = function () {
setTimeout('location.href=location.pathname+location.search.replace(/[\?|&]captcha-challenge/,\'\')', 1500);
document.cookie = '__jsl_clearance=1539775703.479|0|' + (function () {
var _3h = [function (_21) {
return _21
}, function (_3h) {
return _3h
}, (function () {
var _21 = document.createElement('div');
_21.innerHTML = '<a href=\'/\'>_43</a>';
_21 = _21.firstChild.href;
var _3h = _21.match(/https?:\/\//)[0];
_21 = _21.substr(_3h.length).toLowerCase();
return function (_3h) {
for (var _43 = 0; _43 < _3h.length; _43++) {
_3h[_43] = _21.charAt(_3h[_43])
}
;
return _3h.join('')
}
})(), function (_21) {
for (var _3h = 0; _3h < _21.length; _3h++) {
_21[_3h] = parseInt(_21[_3h]).toString(36)
}
;
return _21.join('')
}],
_21 = [[(-~(+[]) + [] + []) + [-~!/!/ + ((+!-[]) << (+!-[])) + 5]], 'mT', [(-~(+[]) + [] + []) + [(-~{} | 2)]], 'wH', [[6]], [(-~(+[]) + [] + []) + [-~[-~!/!/ + ((+!-[]) << (+!-[])) - ~!/!/ + ((+!-[]) << (+!-[]))]]], 'E%', [-~!/!/ - ~!/!/], 'B', [(-~(+[]) + [] + []) + [2 + 2], (-~(+[]) + [] + []) + (-~[] + ((+!-[]) << -~!/!/ + ((+!-[]) << (+!-[]))) + [] + [[]][0])], 'WsAkM', [~~''], 'tCX', [((-~!/!/ - ~!/!/ ^ -~(+[]))) / ~~'' + [] + []][0].charAt(~~!{}), [(-~(+[]) + [] + []) + (-~[] + ((+!-[]) << -~!/!/ + ((+!-[]) << (+!-[]))) + [] + [[]][0])], 'HY', [(-~{} + [~~{}]) / [2]] + [2 + 2], '%', [(-~{} | 2)], 'D'];
for (var _43 = 0; _43 < _21.length; _43++) {
_21[_43] = _3h[[3, 1, 2, 1, 2, 3, 1, 0, 1, 3, 1, 0, 1, 0, 3, 1, 0, 1, 0, 1][_43]](_21[_43])
}
;
return _21.join('')
})() + ';Expires=Wed, 17-Oct-18 12:28:23 GMT;Path=/;'
};
if ((function () {
try {
return !!window.addEventListener;
} catch (e) {
return false;
}
})()) {
document.addEventListener('DOMContentLoaded', _21, false)
} else {
document.attachEvent('onreadystatechange', _21)
}可以马上定位到我们需要的代码片段
'__jsl_clearance=1539775703.479|0|' + (function () {
var _3h = [function (_21) {
return _21
}, function (_3h) {
return _3h
}, (function () {
var _21 = document.createElement('div');
_21.innerHTML = '<a href=\'/\'>_43</a>';
_21 = _21.firstChild.href;
var _3h = _21.match(/https?:\/\//)[0];
_21 = _21.substr(_3h.length).toLowerCase();
return function (_3h) {
for (var _43 = 0; _43 < _3h.length; _43++) {
_3h[_43] = _21.charAt(_3h[_43])
}
;
return _3h.join('')
}
})(), function (_21) {
for (var _3h = 0; _3h < _21.length; _3h++) {
_21[_3h] = parseInt(_21[_3h]).toString(36)
}
;
return _21.join('')
}],
_21 = [[(-~(+[]) + [] + []) + [-~!/!/ + ((+!-[]) << (+!-[])) + 5]], 'mT', [(-~(+[]) + [] + []) + [(-~{} | 2)]], 'wH', [[6]], [(-~(+[]) + [] + []) + [-~[-~!/!/ + ((+!-[]) << (+!-[])) - ~!/!/ + ((+!-[]) << (+!-[]))]]], 'E%', [-~!/!/ - ~!/!/], 'B', [(-~(+[]) + [] + []) + [2 + 2], (-~(+[]) + [] + []) + (-~[] + ((+!-[]) << -~!/!/ + ((+!-[]) << (+!-[]))) + [] + [[]][0])], 'WsAkM', [~~''], 'tCX', [((-~!/!/ - ~!/!/ ^ -~(+[]))) / ~~'' + [] + []][0].charAt(~~!{}), [(-~(+[]) + [] + []) + (-~[] + ((+!-[]) << -~!/!/ + ((+!-[]) << (+!-[]))) + [] + [[]][0])], 'HY', [(-~{} + [~~{}]) / [2]] + [2 + 2], '%', [(-~{} | 2)], 'D'];
for (var _43 = 0; _43 < _21.length; _43++) {
_21[_43] = _3h[[3, 1, 2, 1, 2, 3, 1, 0, 1, 3, 1, 0, 1, 0, 3, 1, 0, 1, 0, 1][_43]](_21[_43])
}
;
return _21.join('')
})()这一块代码我们扔进v8肯定是无法执行的, 因为涉及到了document操作,
(当然,伪造document也不是不行 只是 我们前文提到 这次不使用)
其中不能直接执行的如下
(function () {
var _21 = document.createElement('div');
_21.innerHTML = '<a href=\'/\'>_43</a>';
_21 = _21.firstChild.href;
var _3h = _21.match(/https?:\/\//)[0];
_21 = _21.substr(_3h.length).toLowerCase();
return function (_3h) {
for (var _43 = 0; _43 < _3h.length; _43++) {
_3h[_43] = _21.charAt(_3h[_43])
}
;
return _3h.join('')
}
})()这一段返回的结果是真实访问的网址,替换就行了
data.slice(data.indexOf("'__jsl_clearance"),
data.indexOf("+';Expires")).replace(/document(.*?)toLowerCase\(\)/g, function(y){return '"www.网址.com/"'})加速乐Cookie生成
/*
请在此处放入以下代码
var x="@@@@0@pathname@g@fromCharCode@1541851156@catch@String@cookie@59@try@charAt@d@12@location@4@toString@firstChild@@document@@@@false@@36@Expires@for@@@@e@charCodeAt@@@@challenge@@toLowerCase@@@reverse@@@eval@captcha@@return@onreadystatechange@488@match@chars@@@https@Sat@@@@new@@DOMContentLoaded@createElement@8@@parseInt@search@@2@href@16@@a@1500@if@0xEDB88320@innerHTML@@substr@Nov@length@@@JgSe0upZ@0xFF@@@@div@@GMT@function@else@split@@@@10@@RegExp@Path@1@window@@f@5@addEventListener@while@@Array@join@var@attachEvent@__jsl_clearance@@@@@replace@@setTimeout@@rOm9XFMtA3QKV7nYsPGT4lifyWwkq5vcjH2IdxUoCbhERLaz81DNB6@@18".replace(/@*$/,"").split("@"),y="3j 1c=2v(){3s('i.29=i.6+i.26.3q(/[\\?|&]1h-18/,\\'\\')',2d);n.c='3l=9.1l|5|'+(2v(){3j 2p=[2v(1c){1j 1g('b.8('+1c+')')},2v(1c){v(3j 2p=5;2p<1c.2k;2p++){1c[2p]=25(1c[2p]).k(t)};1j 1c.3i('')}],1c=[[((-~![]+[j]>>-~![])+[])+[(-~-~~~'')*[-~-~~~'']],[(-~-~~~'')*[-~-~~~'']]+(-~[28+3d]+[]+[[]][5]),(-~[28+3d]+[]+[[]][5])+(-~[28+3d]+[]+[[]][5])],[((+!+{})+[[]][5])+((-~[]|(+!+{})+(+!+{}))+(-~[]|(+!+{})+(+!+{}))+[]),[(+!+{})+(+!+{})]+[(+!+{})+(+!+{})],[(+!+{})+(+!+{})]+((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])],[(-~[28+3d]+[]+[[]][5])+((-~[]|(+!+{})+(+!+{}))+(-~[]|(+!+{})+(+!+{}))+[]),[28+((-~![]<<-~![])^(+!+{}))]+((-~![]+[j]>>-~![])+[]),(-~[28+3d]+[]+[[]][5])+[(-~[]|(+!+{})+(+!+{}))+[-~-~~~'']*((-~[]|(+!+{})+(+!+{})))]],[((+!+{})+[[]][5])+[(-~-~~~'')*[-~-~~~'']]],[((-~![]+[j]>>-~![])+[])+((+!{})+[[]][5]),((-~![]+[j]>>-~![])+[])+[(-~[]|(+!+{})+(+!+{}))+[-~-~~~'']*((-~[]|(+!+{})+(+!+{})))],((-~![]+[j]>>-~![])+[])+[(-~-~~~'')*[-~-~~~'']]],[((+!+{})+[[]][5])+((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])],[(-~[28+3d]+[]+[[]][5])+[28+((-~![]<<-~![])^(+!+{}))],((-~![]+[j]>>-~![])+[])+[28+((-~![]<<-~![])^(+!+{}))],((-~![]+[j]>>-~![])+[])+((-~[]|(+!+{})+(+!+{}))+(-~[]|(+!+{})+(+!+{}))+[]),[28+((-~![]<<-~![])^(+!+{}))]+((+!+{})+[[]][5])],[((+!+{})+[[]][5])+[28+((-~![]<<-~![])^(+!+{}))]],[((-~![]+[j]>>-~![])+[])+((+!+{})+[[]][5])],[((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])+((+!{})+[[]][5]),((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])+[(+!+{})+(+!+{})]],[[(-~[]|(+!+{})+(+!+{}))+[-~-~~~'']*((-~[]|(+!+{})+(+!+{})))]+((+!{})+[[]][5])],[((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])+((+!+{})+[[]][5])],[(-~[28+3d]+[]+[[]][5])+((-~[]|(+!+{})+(+!+{}))+(-~[]|(+!+{})+(+!+{}))+[]),[28+((-~![]<<-~![])^(+!+{}))]+[(+!+{})+(+!+{})],[28+((-~![]<<-~![])^(+!+{}))]+[(+!+{})+(+!+{})],((-~{}+[-~-~~~'']>>-~-~~~'')+[]+[[]][5])+((-~![]+[j]>>-~![])+[]),[28+((-~![]<<-~![])^(+!+{}))]+((+!+{})+[[]][5]),((-~[]|(+!+{})+(+!+{}))+(-~[]|(+!+{})+(+!+{}))+[])+(-~[28+3d]+[]+[[]][5])]];v(3j 1p=5;1p<1c.2k;1p++){1c[1p]=2p.1d()[((+!+{})+[[]][5])](1c[1p])};1j 1c.3i('')})()+';u=1r, 35-2j-40 h:d:2a 2u;38=/;'};2e((2v(){e{1j !!3a.3e;}a(13){1j r;}})()){n.3e('21',1c,r)}30{n.3k('1k',1c)}",f=function(x,y){var a=0,b=0,c=0;x=x.split("");y=y||99;while((a=x.shift())&&(b=a.charCodeAt(0)-77.5))c=(Math.abs(b)<13?(b+48.5):parseInt(a,36))+y*c;return c}}
*/
function getJSL() {
var z = f(y.match(/\w/g).sort(function (x, y) {
return f(x) - f(y)
}).pop());
var data = "";
var initZ = z;
while (data.indexOf("document.cookie='__jsl") == -1 && z++ - initZ < 20) {
data = y.replace(/\b\w+\b/g, function (y) {
return x[f(y, z) - 1] || ("_" + y)
});
}
;
console.info(data.slice(data.indexOf("'__jsl_clearance"), data.indexOf("+';Expires")))
return eval(data.slice(data.indexOf("'__jsl_clearance"), data.indexOf("+';Expires")).replace(/document(.*?)toLowerCase\(\)/g, function (y) {
return '"www.gsxt.gov.cn/"'
}));
}
console.info(getJSL());本文转于冷月文摘,作者还写了一系列的校验破解,感兴趣的可以看看via
原文连接:加速乐Cookie破解与生成__jsl_clearance
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。